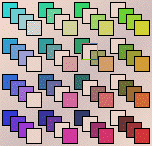| If we have the 2-step memory table, we have seen how to recognize a
2-step memory table whose IFS can be generated by a 1-step
memory table. |
| Suppose we have only the IFS image. How can we tell if this image can be
generated by 1-step memory? |
| Recall that for an IFS generated by 1-step memory, every forbidden combination must contain a
forbidden pair. |
| That is, the address of every empty square must contain an empty length 2 address. |
| One approach is to superimpose the length 3 address grid, note the empty length 3 addresses, and note the
empty length 2 addresses. |
| If some empty length 3 address does not contain an empty length 2 address, we are finished. |
| If every empty length 3 address contains an empty length 2 address, and if we know the image is
generated by 2-step memory, then we are finished. |
| If every empty length 3 address contains an empty length 2 address, and if we know the image is
generated by 2-step memory, then we must continue, checking empty length 4, 5, etc addresss. |
| |
| Here is the image with grid for this problem. |
 |
| Note the empty length 2 addresses are 14, 23, and 32. |
| Note also the addresses 412 and 413 are empty. Consequently, this image cannot be generated by a 1-step memory IFS. |
| |
| Here is the 2-step memory table generating this image. Note this table does not satisfy the
condition mentoned above. |
|